Tor Browser: A Journey Through Privacy and Anonymity
introduction
Tor Browser is a powerful tool for communicating anonymously over the Internet. It provides some privacy by navigating your Internet through volunteer-operated relays that are decentralized. In this article, we explore the history, current state, and possible future of the Tor Browser.
What is onion tracing?
Onion routing is a method of communicating anonymously electronically. It provides high levels of security and privacy by encrypting messages in encryption layers such as onion layers. Let me explain how it works:
Encapsulation: When someone sends a message through the onion network, the message is wrapped with several layers of encryption. Each layer corresponds to an intermediary node (called an “onion router”) through which the message will pass.
Routing: Encrypted messages pass through these onion routers. At each step, the onion router removes an encryption, revealing the next destination of the message. The router only knows the location of the first and immediately following nodes, ensuring that the sender remains anonymous.
Final decryption: When the final stage of encryption is removed, the message reaches its intended destination. The receiver can decrypt the message and read its contents.

history
The concept of onion routing emerged in the mid-1990s in response to growing concerns about Internet security and surveillance. Researchers in the U.S. The Naval Research Laboratory (NRL), with David Goldschlag, Mike Reid, and Paul Syverson, is looking for a way to create an Internet connection that doesn't tell who is communicating with whom—even to network administrators -through do so , encrypted at every step. This basic concept remains the basis of how Tor works today
In the early 2000s, Roger Dingledin and Nick Mathewson co-created the Tor network. To differentiate their work from other onion routing projects, they named it “Tor”, meaning “The Onion Routing”. Tor’s decentralized network was essential, manned by organizations with different interests and trust ratios. In October 2002, the Tor network was implemented, and its code was released under a free open-source software license. By the end of 2003, there were about a dozen volunteer groups, mainly in the US. and Germany.
Recognizing Tor's digital rights potential, the Electronic Frontier Foundation (EFF) began funding its development in 2004. To maintain Tor's development, the Tor Project, Inc., a non-profit organization, was founded search for profit, in 2006. Tor's influence grew exponentially, especially in the 2010s During the Arab Spring at the end of the year, it not only protected users online but also provided access to resources important that would prevent, social media as well as websites
today
Tor has come a long way since its early days. Here are some of the main features of Tor today.
Tor network: The Tor network consists of thousands of relays operated by volunteers around the world. When you use Tor, your internet traffic takes random routes, making it hard to trace your online activity.
Tor Browser: The Tor Browser is a user-friendly interface that allows you to connect to the Tor network. It comes with built-in privacy settings like HTTPS-Only mode and NoScript. Tor Browser makes it easier for everyday users to take advantage of Tor's privacy protections
Usage: Tor is used by professionals, journalists, whistleblowers, and privacy-minded individuals. This allows them to securely communicate, view content, and protect their identity.
future
Looking ahead, Tor has many exciting possibilities for the future:
Improved usability: Continued efforts to make the Tor Browser more user-friendly will make it more widely available. Simplified installation and configuration will encourage more users to adopt Tor.
Scalability: As internet censorship and surveillance continues, Tor scalability becomes increasingly important. Expanding the network and ensuring it can withstand attacks will be important.
Mobile integration: Tor integration with mobile devices could revolutionize privacy on smartphones. Efforts are already underway to develop Tor for Android and iOS.
Privacy innovation: Tor’s research team is constantly looking for new technologies that enhance privacy. Improvements in areas such as anonymous certificates, decentralized name systems, and better encryption will determine the future of Tor.
How to download Tor Browser
Follow these steps to download the Tor Browser.
Visit the Tor Project website: Visit the official Tor Project website by typing “torproject.org” in the address bar of your browser.
Download Tor Browser: Click on the “Download Tor Browser” button in the top right corner of the website.
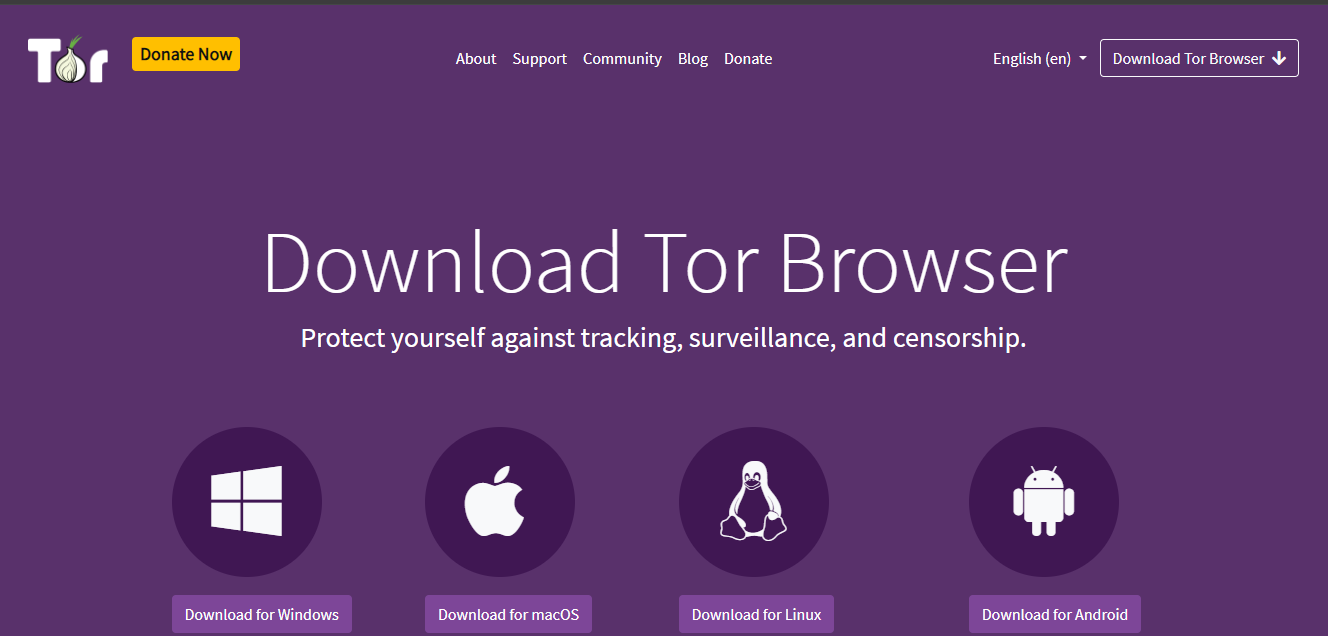
Choose your operating system: Choose the right one for your operating system (Windows, macOS, Linux, or Android).
Verify the download (recommended): After downloading, verify the file signature to ensure authenticity. You can find instructions on how to verify signatures in the Tor Browser manual.
Remember: Privacy is not a luxury; it is a special privilege.
Browsers for Android: Privacy and Freedom on the Internet
Tor Browser for Android is the official mobile browser sponsored by The Tor Project, a non-profit organization dedicated to advancing human rights and freedoms online If you are concerned about tracking, surveillance, and censorship, Tor Browser offers a powerful solution. Here’s what you need to know.
Tor Browser for Android
Privacy and anonymity: Tor Browser isolates any website you visit, preventing you from being tracked by third-party trackers and ads. Any cookies will be deleted during browsing.
Protect against monitoring: The Tor browser ensures that anyone monitoring your browsing habits can only see that you are using Tor, not the specific website you visit.
Fingerprint resistance: Tor aims to standardize all users, making it harder for you to obtain a fingerprint based on your browser and device information.
Multi-layer encryption: When you use the Tor browser for Android, your traffic is relayed and encrypted three times as it travels over the Tor network. The network consists of thousands of servers operated by volunteers called Tor relays.
How to download Tor Browser for Android
Google Play Store: You can download the Tor Browser directly from the Google Play Store or click here
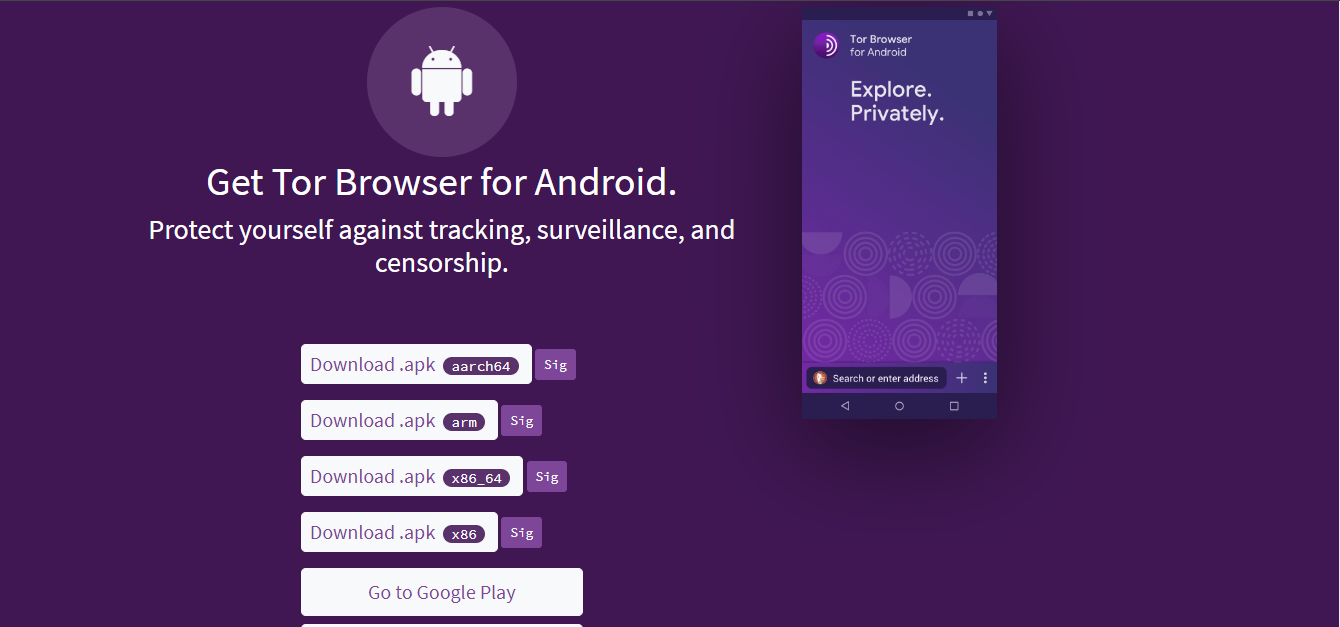
F-Droid repository: Alternatively, you can access the Tor Browser from the F-Droid repository. Install the F-Droid app on your Android device, then open it and go to “Settings”. Then select Tor Browser.
Remember, Tor Browser is free open-source software developed by The Tor Project. Your support helps keep Tor strong, safe, and independent. Consider contributing to the advancement of privacy and freedom online
Orbot: Increases privacy on Android
Apart from Tor Browser, another valuable tool for Android users is Orbot. Developed by The Guardian Project, Orbot empowers other apps on your device to use the internet more efficiently. Here's what you need to know about Orbot:
Encryption and Anonymity :
- Orbot uses Tor to encrypt and encrypt your internet traffic by bouncing it across a series of computers around the world.
- It works seamlessly with other apps on your device to protect your privacy.
- Avoid censorship: Orbot routes traffic from web browsers, email clients, map programs and other apps over the Tor network, bypassing censorship
- Open Source: Orbot is free and open-source software, intended for use by human rights activists, journalists and privacy-minded individuals around the world.
- To download Orbot, visit the official Orbot website or click here

Leave a Reply